Vulnerability Management
Your Risk Ends Here.
Know your weaknesses. Reveal Gaps. Close Vulnerabilities Quickly. Effective vulnerability management identifies, assesses, and mitigates weaknesses to protect your organization from potential threats
Breach & Attack Simulation
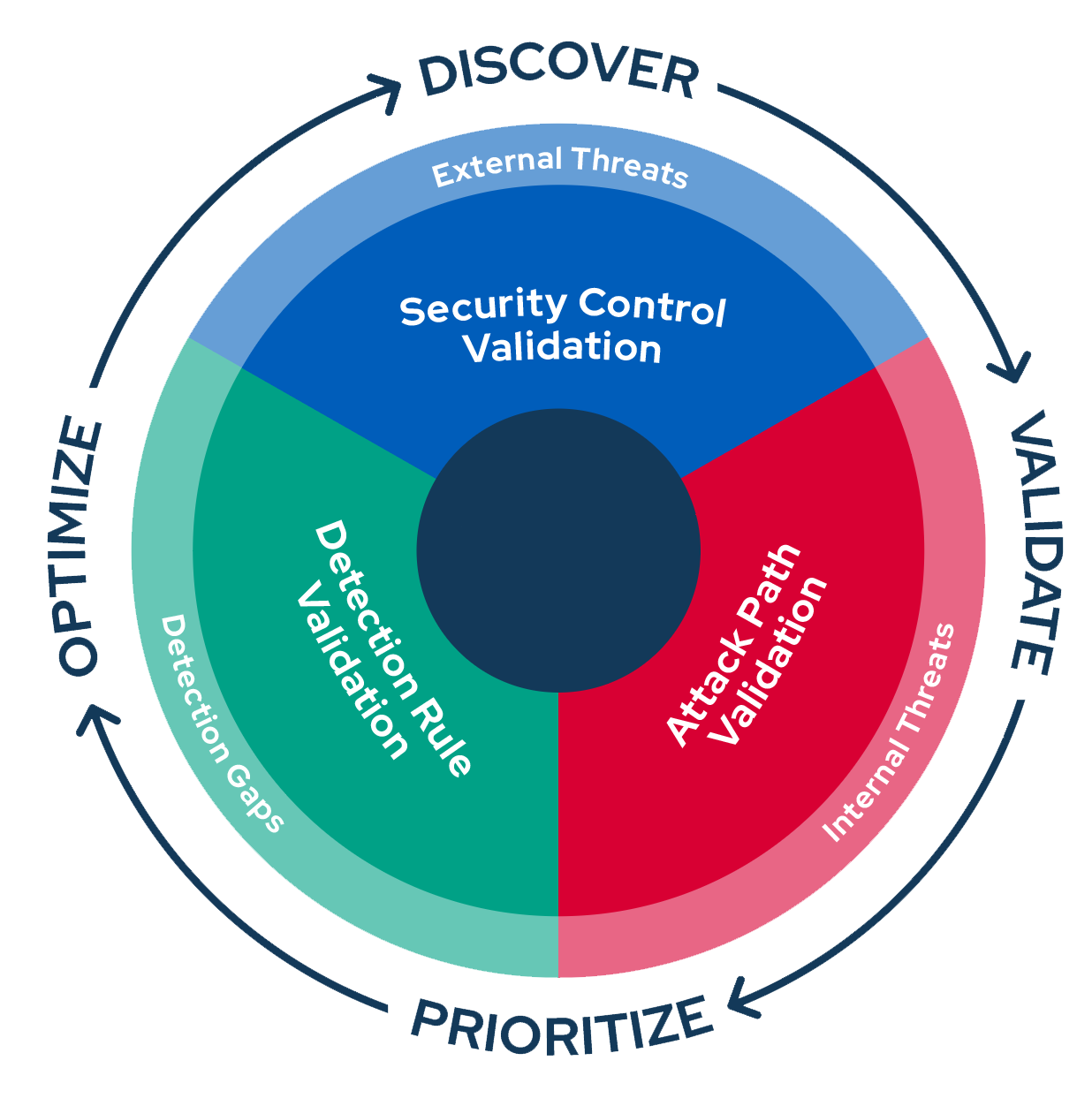
Automatically and continuously validate the effectiveness of your prevention and detection controls.
Stop attackers in their tracks by eliminating routes to critical users and assets.
Proactively identify issues related to the performance and hygiene of SIEM rules and obtain insights to accelerate threat detection and response.
Enhance security visibility across your attack surface and uncover hidden risks.
Extend security validation to the cloud with automated cloud assessment and attack simulation.
Insider Threat Detection: Real-Time Detection and Response
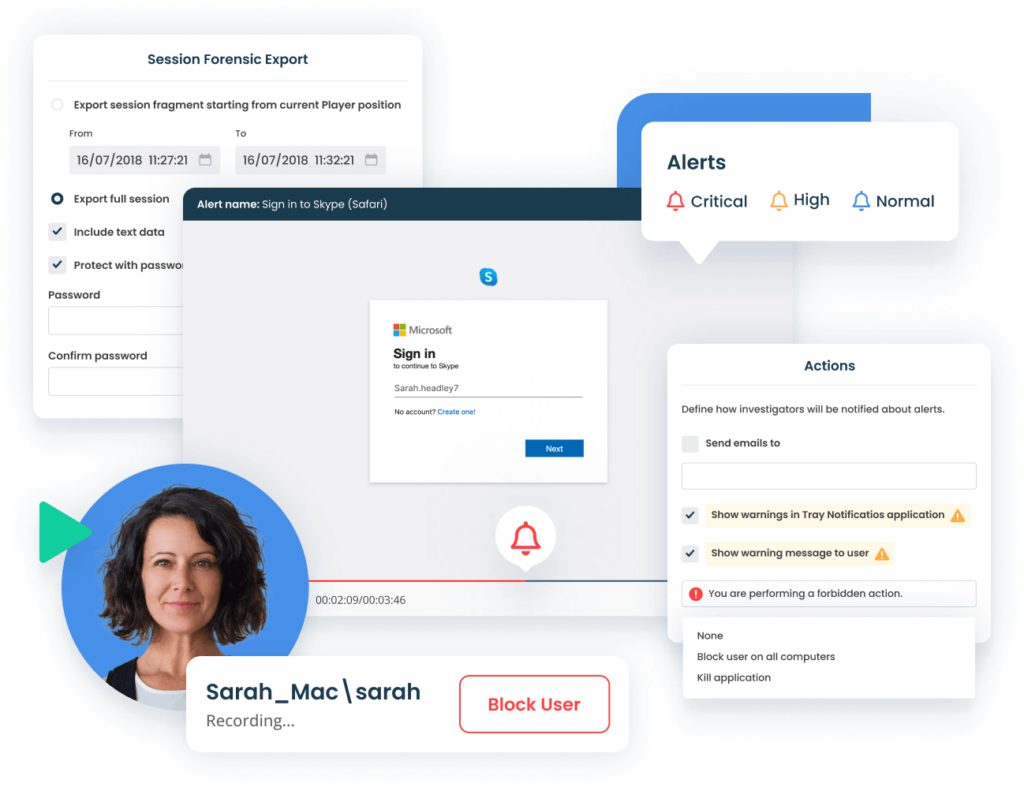
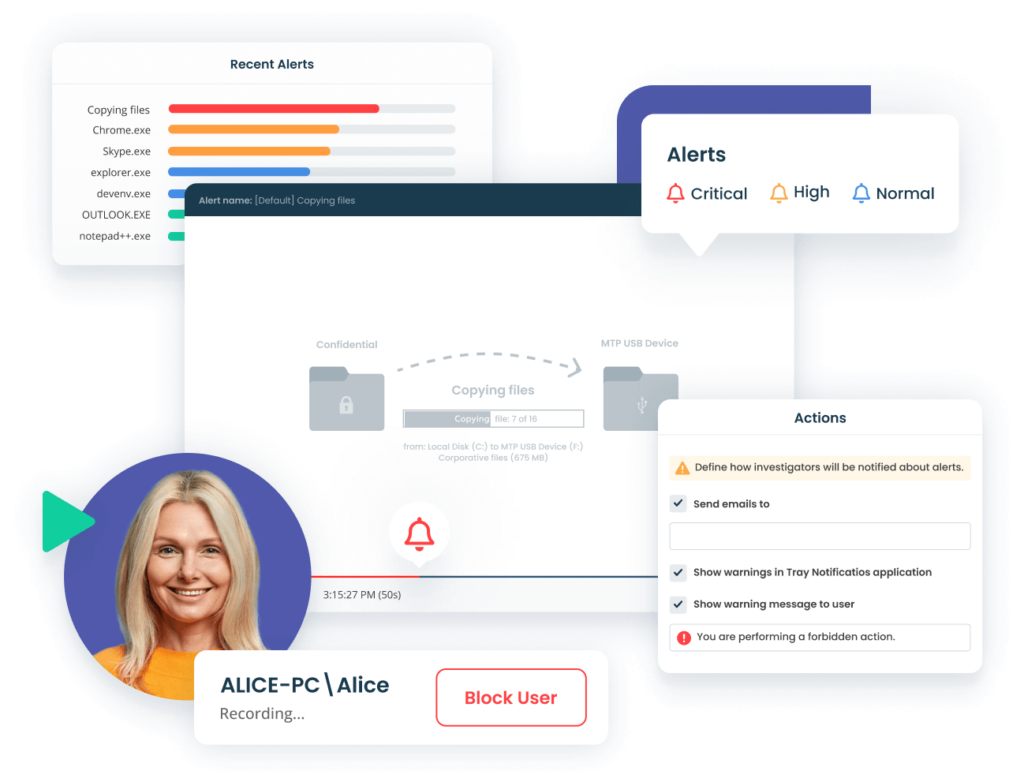
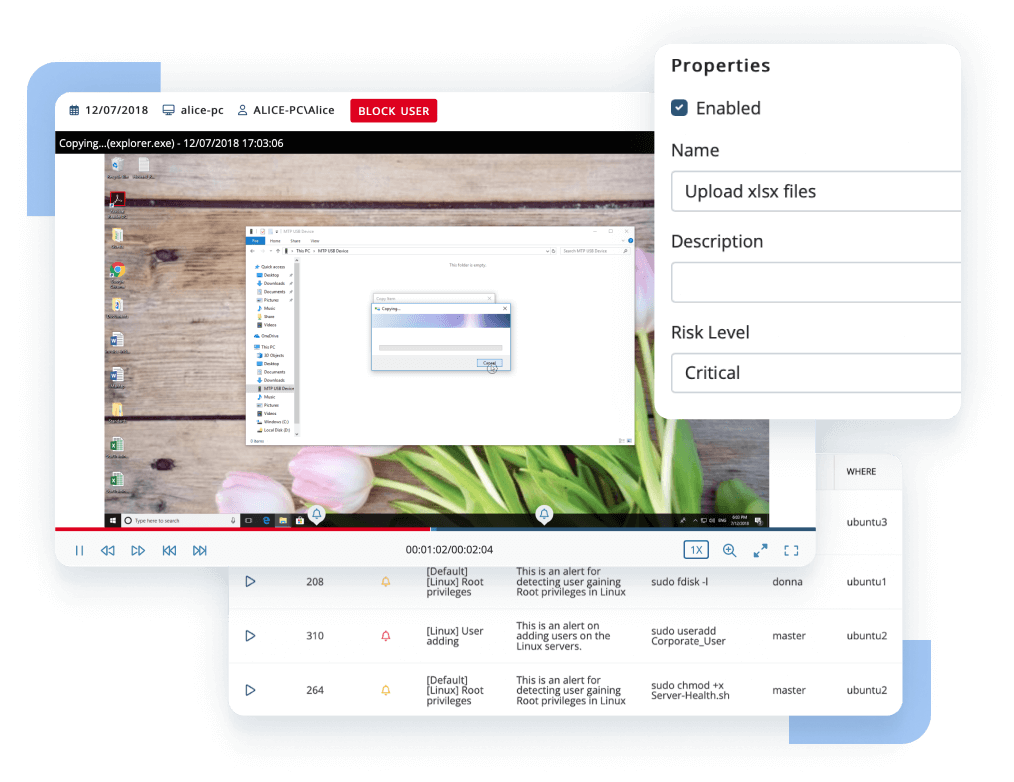
User Activity Monitoring
Monitor insider activity. Detect anomalies. Respond to incidents. ALL-IN-ONE
Predefined and Custom Alerts
A comprehensive insider threat detection solution includes rule-based incident flagging with a collection of alert templates that cover common insider threat indicators. You can also customize the system with your own alert rules using various activity parameters, such as process names, opened web addresses, connected USB devices, typed keystrokes, or executed Linux commands.
Phising Management
Risk Identification
Phishing simulations help organizations identify which employees or departments are most vulnerable to phishing attacks, enabling targeted training and support.
Real-World Scenarios
These simulations replicate actual phishing tactics, providing employees with hands-on experience in recognizing and responding to phishing threats.
Behavioral Change
By exposing employees to simulated phishing attacks, organizations can promote positive behavioral changes, encouraging safer online practices.
Performance Tracking
Organizations can monitor and evaluate employee responses to phishing simulations, gaining valuable insights into the effectiveness of security measures and identifying areas for improvement.
Security Awareness Training
Security awareness programs educate employees on recognizing threats like phishing and malware, and reinforce the importance of adhering to organizational security policies. These programs also prepare employees for proper incident response and promote continuous improvement in cybersecurity practices.


Employee Education
Security awareness programs educate employees about the importance of cybersecurity, teaching them how to recognize and avoid potential threats such as phishing, malware, and social engineering attacks.

Policy Adherence
These programs reinforce the importance of following organizational security policies, such as using strong passwords, avoiding unsecured networks, and adhering to data protection regulations.

Incident Response
Security awareness training helps employees understand how to respond if they encounter a security threat, including reporting incidents promptly and following the proper procedures to mitigate risks.

Continuous Improvement
Regular security awareness initiatives ensure that employees stay updated on the latest threats and best practices, fostering a culture of continuous improvement in cybersecurity within the organization.
