Attackers Don't Hack In, They Log In.

Robust multi-factor authentication and security control.
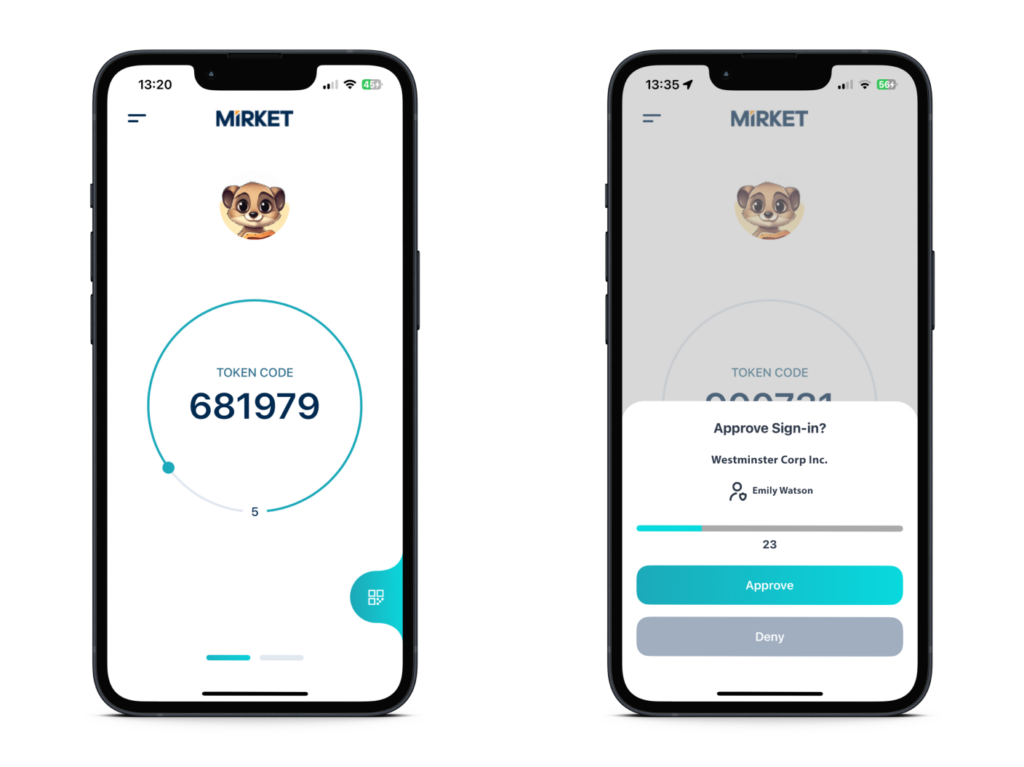
Ensure the security of critical corporate data while reducing management time and business costs with Mirket Mobile. Our solution offers secure authentication during login through a variety of methods, including Mirket Token, Online OTP code, TOTP code, or a simple one-touch sign-in. Mirket Mobile also features device trust, continuously verifying the safety of installed devices to protect against unauthorized access.
Mirket’s Multi-Factor Authentication (MFA) solution achieves an optimal balance between security and user experience. Our diverse range of flexible authentication methods allows you to customize security measures to fit various business needs and user preferences, ensuring robust protection while maintaining ease of use.
Enhancing security doesn’t have to be complex. Mirket enables you to implement robust authentication in just minutes. Our solution supports seamless integrations with VPNs, applications like Office 365, and offers user-friendly APIs for a hassle-free deployment. Additionally, self-service options for end-users and straightforward administration streamline your MFA implementation, making it both efficient and user-friendly.
Single Sign-On (SSO)
Centralized Authentication
Authentication and access are managed centrally from one location.

Adapt and Respond to Risks in Real Time
Risk-Based Authentication adjusts security requirements in real time based on threat signals, protecting trusted users and blocking attackers.

Single Sign-On (SSO)
Provide secure access to any app from a single dashboard.
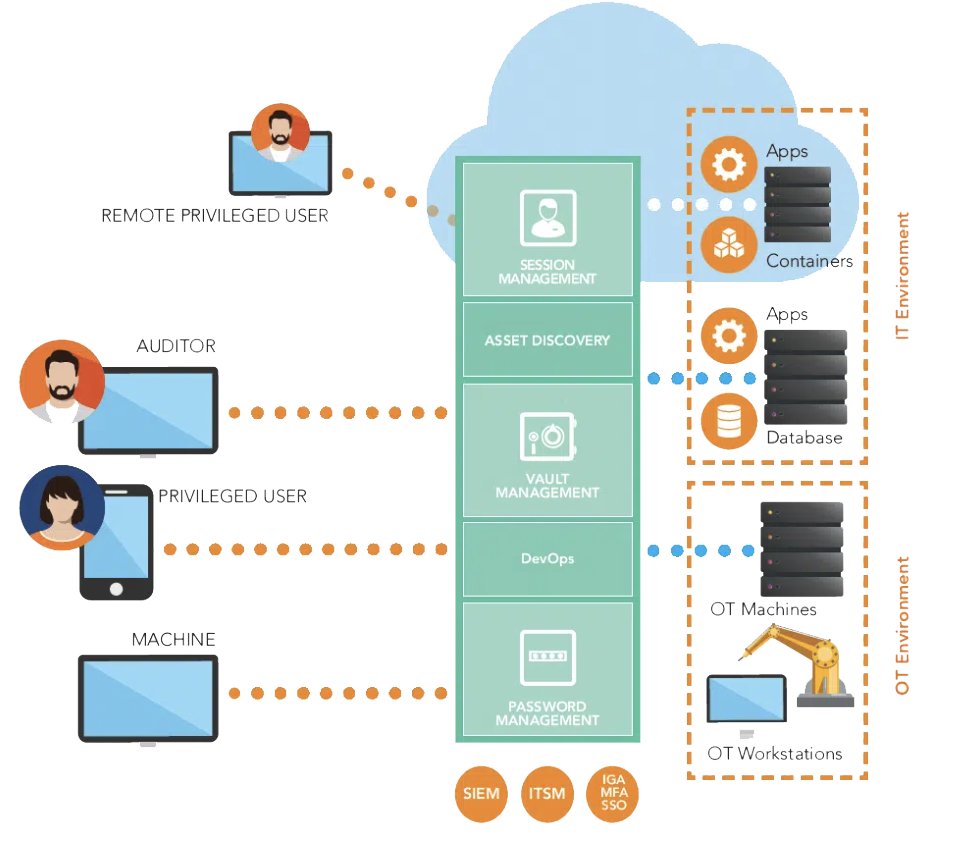
Privileged Access Management - PAM

Securing Privileged Accounts
Privileged Access Management (PAM) is designed to manage and secure privileged accounts within an organization’s IT and OT environments. These accounts, often held by administrators, IT personnel, third-party vendors, or used by software and machines, have elevated permissions and provide access to critical systems and sensitive data.

Strengthening Cybersecurity with PAM
PAM focuses on controlling, monitoring, and securing access to these accounts to reduce the risk of unauthorized access, data breaches, or misuse of sensitive information. Overall, PAM strengthens an organization’s cybersecurity posture by managing access to critical systems, mitigating insider threats, and ensuring regulatory compliance
