Make the internet secure and reliable for your business
5 threats found





















Make the internet secure and reliable for your business
By offering a full suite of network, security, and cybersecurity solutions, we ensure your business operates in a secure and reliable digital environment, safeguarding your critical assets from evolving threats.
Solutions for every security goal
Lineup’s scalable solutions adapt to your needs, ensuring robust protection without compromise.
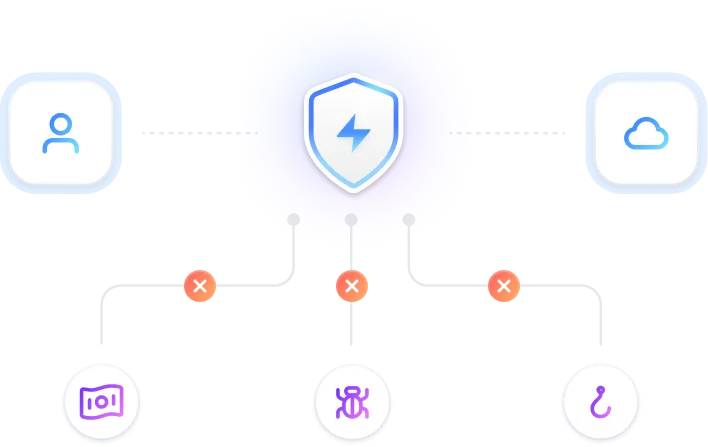
Infrastructure and Network Security
Endpoint and Mobile Security
Data Security
Application Security
OT Security
Threat Management
Cloud Security
Risk Management
Identity and Access Management
Monitoring and Observability
Securing Your Future, Today.
Lineup Services provides comprehensive security solutions tailored to safeguard your business from evolving threats, empowering you to focus on innovation and growth with confidence.


Services
Managed Security Services
Services
Managed Detection and Response
24/7 threat detection and expert response, keeping you secure
Services
NOC and Maintenance Services
Round-the-Clock Monitoring for Reliable Performance.
Services
Pentesting Services
Uncover vulnerabilities and strengthen your security with thorough pentesting.
Services
Managed Security Services
Services
Managed Detection and Response
24/7 threat detection and expert response, keeping you secure
Services
NOC and Maintenance Services
Round-the-Clock Monitoring for Reliable Performance.
Services
Pentesting Services
Uncover vulnerabilities and strengthen your security with thorough pentesting.
